

The subnet mask is the term information technology in the English language that refers to the 32-bit binary number that is used to distinguish the network ID with the host ID, indicating the location of a host, whether on a local network or outside network.
for setting the subnet mask, you specify want to create a subnet with what class. I mean, its IP class. For example:
subnet mask: 255.0.0.0 <--- class A subnet mask subnet mask: 255.255.0.0 <--- class B subnet mask subnet mask: 255.255.255.0 <--- class C subnet mask * Class A subnet can be built as many as 256 x 256 = 65 536, with the total number who could be using that computer's IP on the network is 16,387,064 class A IP address. * subnet a class B subnet 256 can be constructed, with the total number of IP a computer on the network is 64 516 class B IP address. subnet mask IP addresses that follow. # IP address Setting up the IP address where mao IP class (A, B, C). For computer network with computer sum <256 computers, better IP pk class C. Saving network resources. NB: To check the configuration of IP address, subnet mask, gateway, open a command prompt, type "ipconfig". IP Address Subnetting Class A

Subnetting a class B IP address
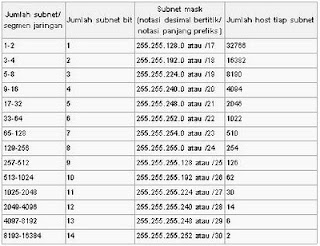
Subnetting Class C IP Address

A subnet mask is usually expressed in dotted decimal notation (dotted decimal notation), as well as IP addresses. After all bits set as the network ID and host ID, the 32-bit value will be converted to dotted decimal notation. It should be noted, that although represented as a dotted decimal notation, the subnet mask is not an IP address.
Classes address Subnet mask (binary) Subnet mask (decimal)
Class A 255.0.0.0 11111111.00000000.00000000.00000000
Class B 255.255.0.0 11111111.11111111.00000000.00000000
Class C 255.255.255.0 11111111.11111111.11111111.00000000
Representation of prefix length (prefix length) of a subnet mask
Classes address Subnet mask (binary) Subnet mask (decimal) Length Prefix
Class A 255.0.0.0 11111111.00000000.00000000.00000000 / 8
Class B 255.255.0.0 11111111.11111111.00000000.00000000 / 16
Class C 255.255.255.0 11111111.11111111.11111111.00000000 / 24
Determining the Network address Identifier
P lamat 10000011 01101011 10100100 00011010 (131107164026)
Subnet Mask 11111111 11111111 11110000 00000000 (255255240000)
-------------------------------------------------- ----------------
Network ID 10000011 01101011 10100000 00000000 (131107160000)




